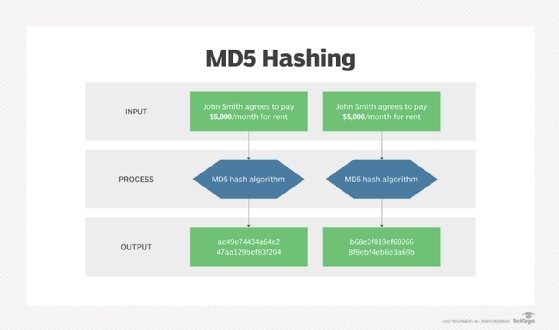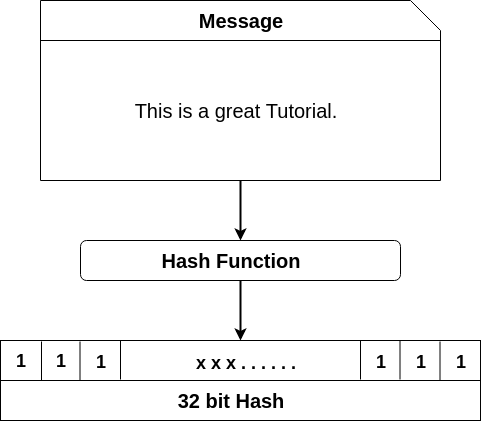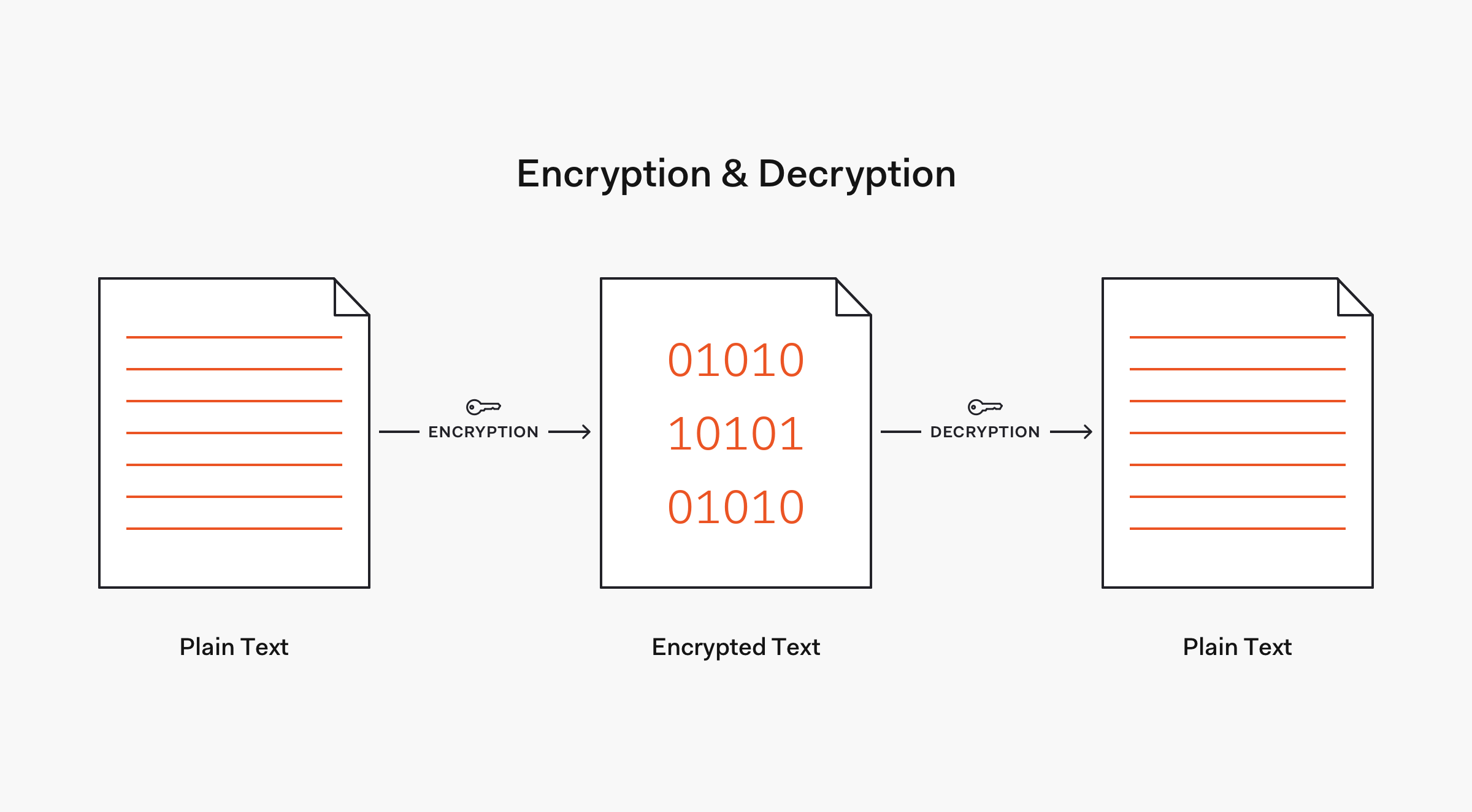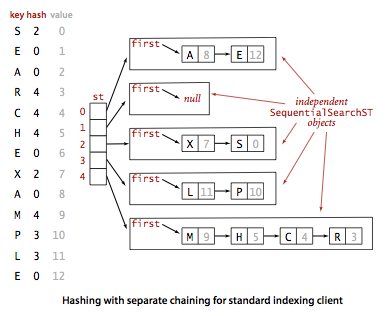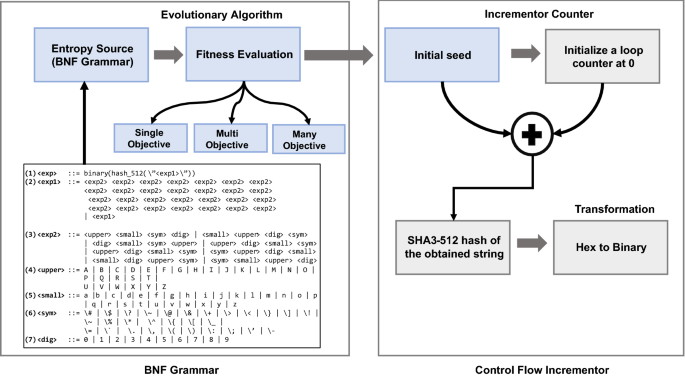
Design of a cryptographically secure pseudo random number generator with grammatical evolution | Scientific Reports

The Problem With Passwords…. A couple of comments I received… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium