
An Automated Framework for Analysis and Evaluation of Algebraic Fault Attacks on Lightweight Block Ciphers | SpringerLink
Computers | Free Full-Text | Comparing the Cost of Protecting Selected Lightweight Block Ciphers against Differential Power Analysis in Low-Cost FPGAs | HTML

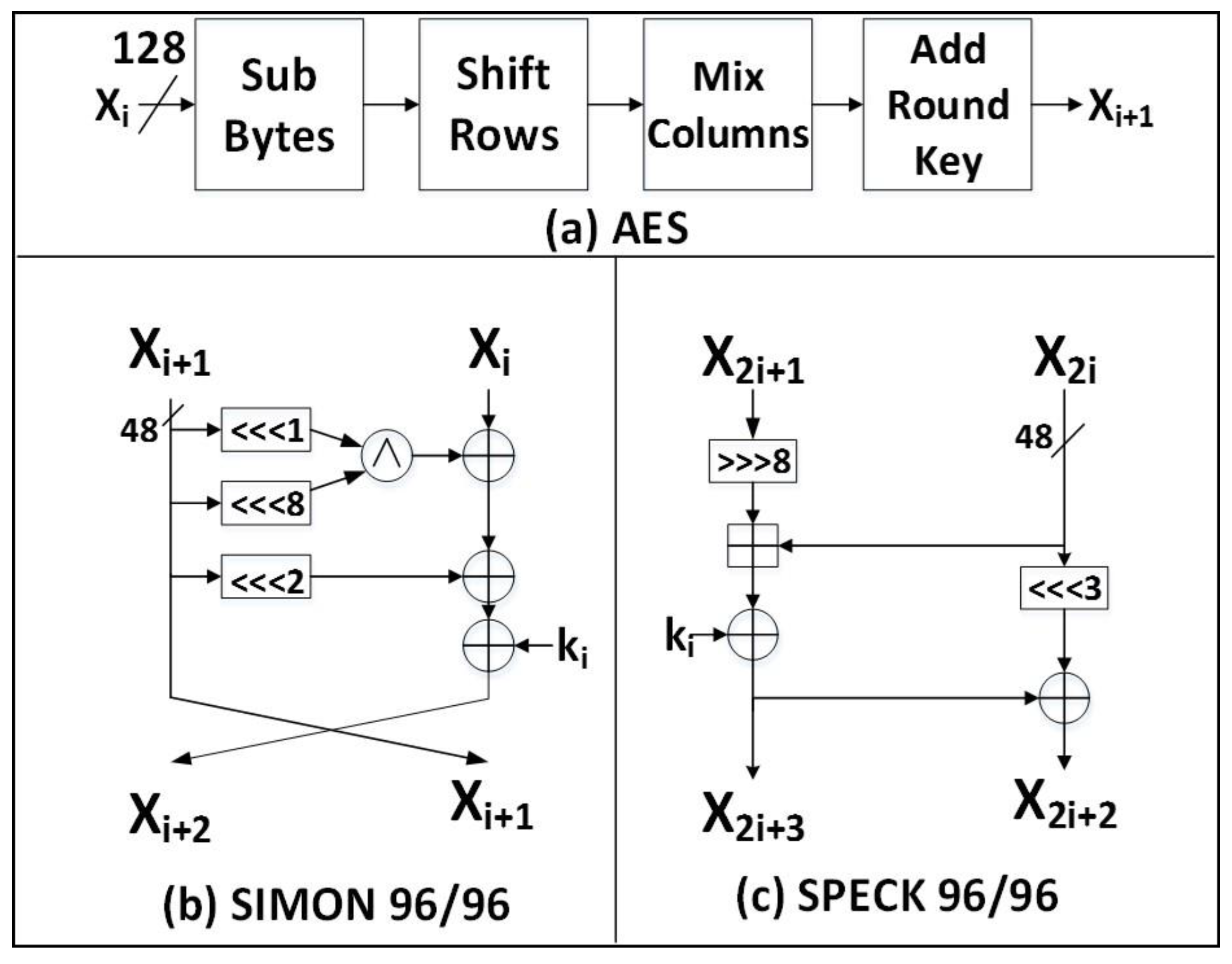
Improved Algebraic Fault Analysis: A Case Study on Piccolo and Applications to Other Lightweight Block Ciphers | SpringerLink



![PDF] Algebraic Differential Fault Attacks on LED using a Single Fault Injection | Semantic Scholar PDF] Algebraic Differential Fault Attacks on LED using a Single Fault Injection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ce85d8d51b3b5178b6f5aae0a9f000cb2724f13e/8-Figure3-1.png)
![PDF] Algebraic Differential Fault Attacks on LED using a Single Fault Injection | Semantic Scholar PDF] Algebraic Differential Fault Attacks on LED using a Single Fault Injection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ce85d8d51b3b5178b6f5aae0a9f000cb2724f13e/3-Figure1-1.png)



![PDF] Algebraic Differential Fault Attacks on LED using a Single Fault Injection | Semantic Scholar PDF] Algebraic Differential Fault Attacks on LED using a Single Fault Injection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ce85d8d51b3b5178b6f5aae0a9f000cb2724f13e/4-Figure2-1.png)

![PDF] Algebraic Differential Fault Attacks on LED using a Single Fault Injection | Semantic Scholar PDF] Algebraic Differential Fault Attacks on LED using a Single Fault Injection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ce85d8d51b3b5178b6f5aae0a9f000cb2724f13e/6-Table1-1.png)