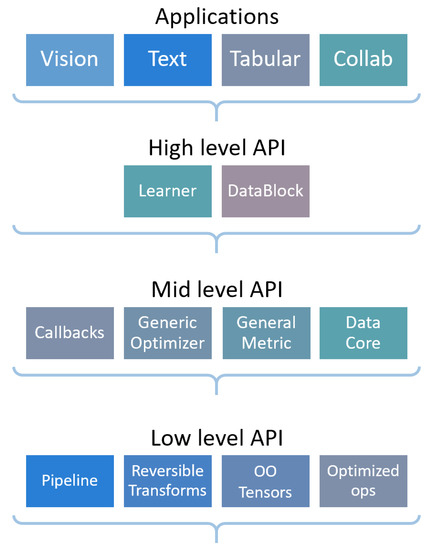
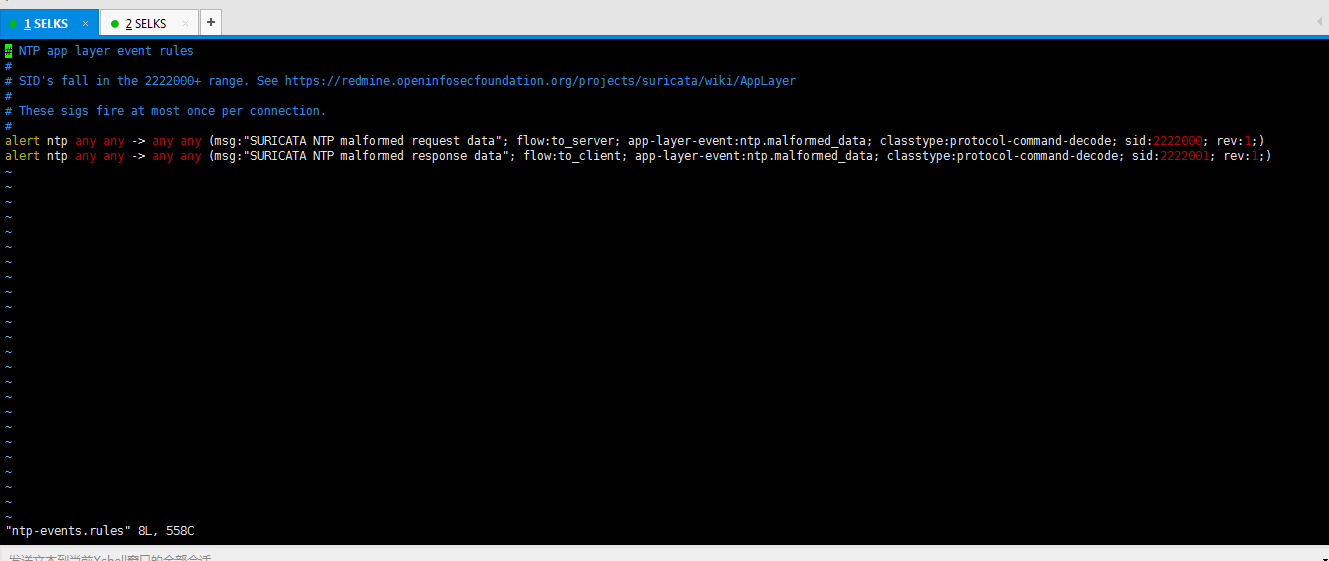
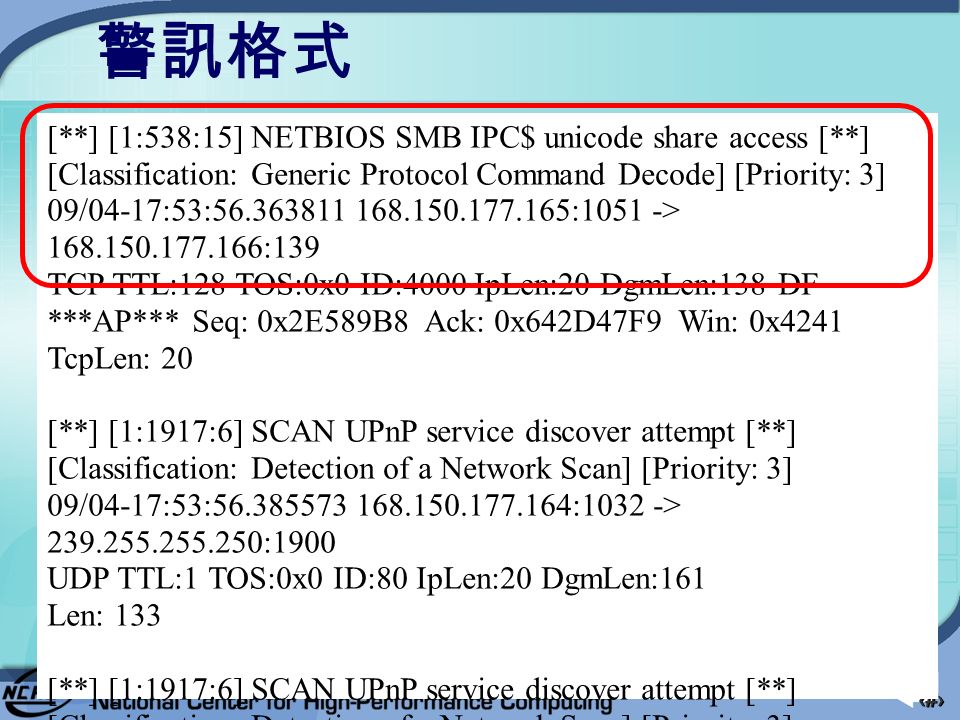
DATE: 05/08/2009 Wei-Yu Chen, Yao-Tsung Wang National Center for High-Performance Computing, Taiwan Building ICAS with Hadoop and. - ppt download

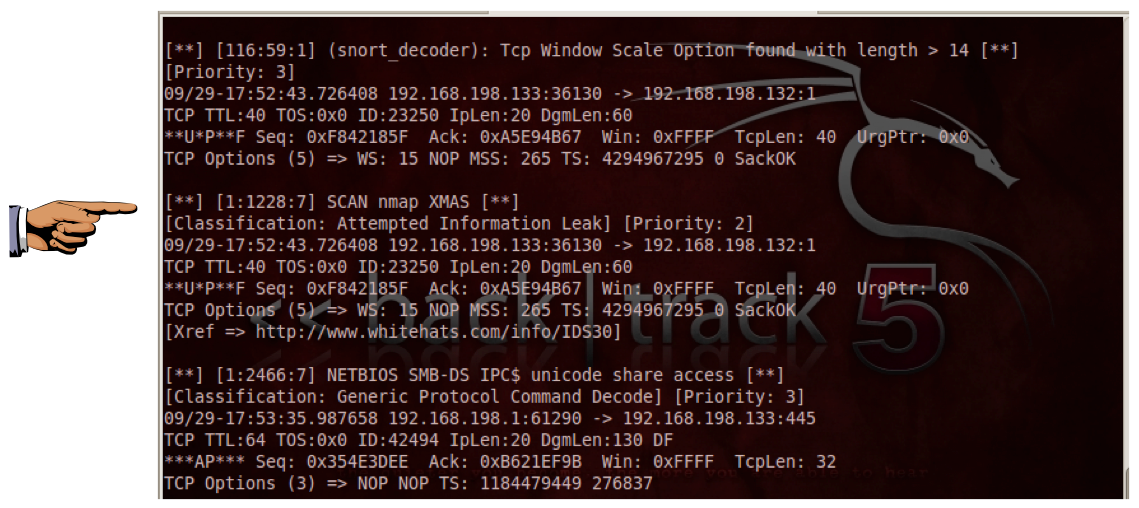
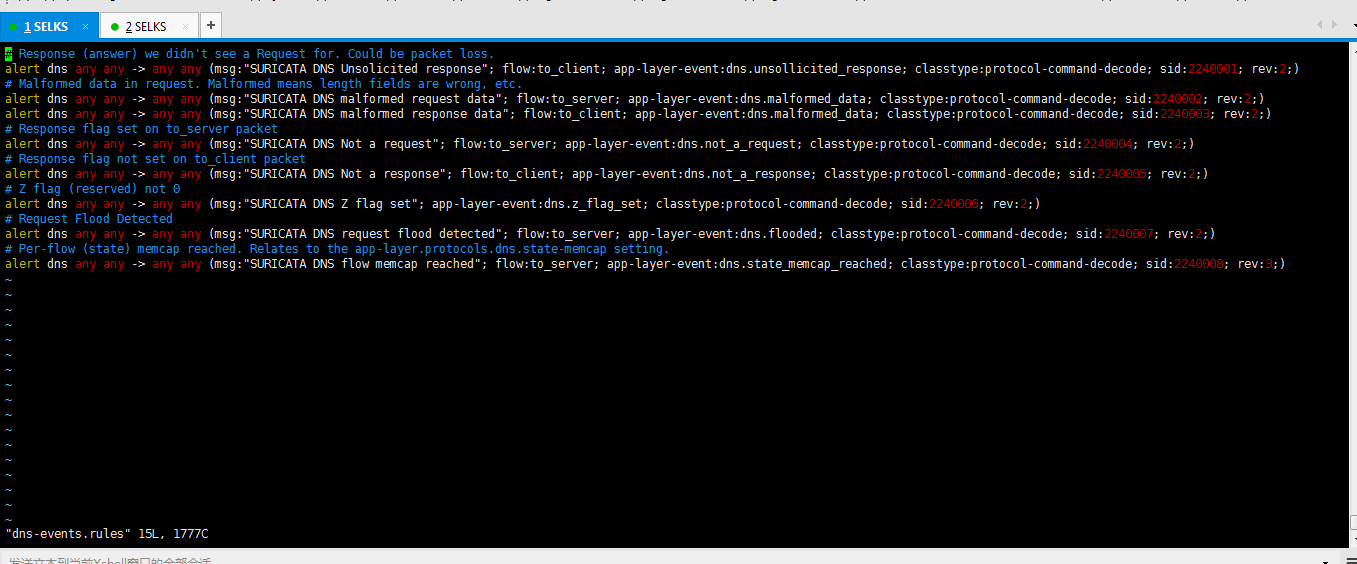
demonstrates extracts of Syslog that has logged the observations from... | Download Scientific Diagram
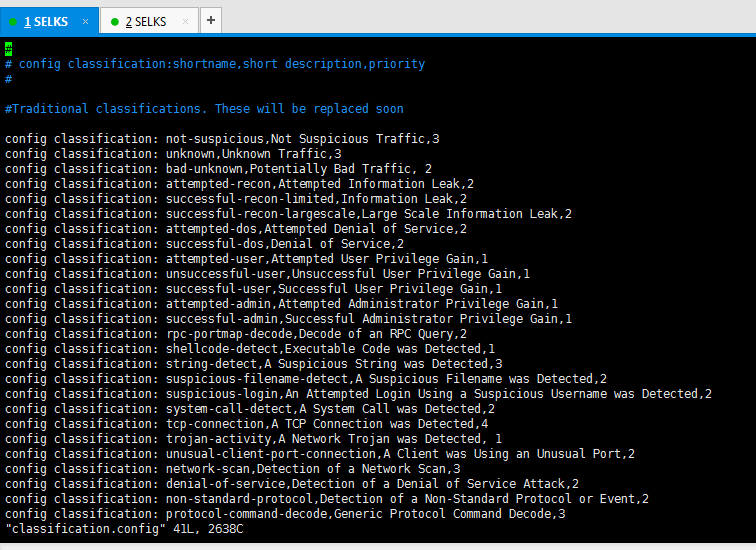
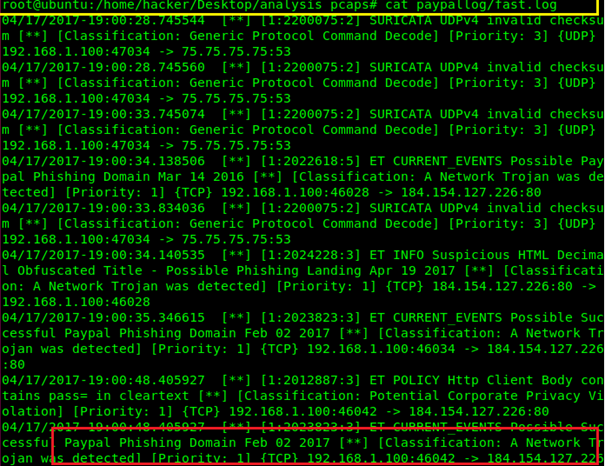
![PDF] Extending Signature-based Intrusion Detection Systems WithBayesian Abductive Reasoning | Semantic Scholar PDF] Extending Signature-based Intrusion Detection Systems WithBayesian Abductive Reasoning | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/96e850985fb59d309bb758c53026fb65aaa2c3db/9-Table8-1.png)
PDF] Extending Signature-based Intrusion Detection Systems WithBayesian Abductive Reasoning | Semantic Scholar
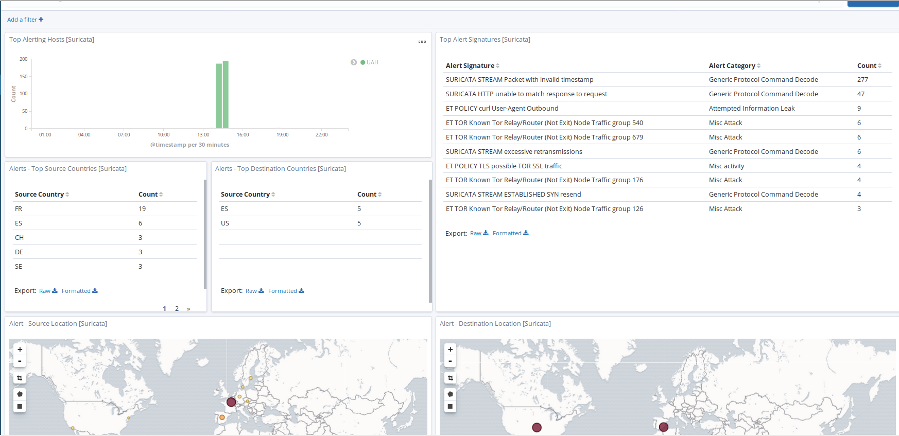
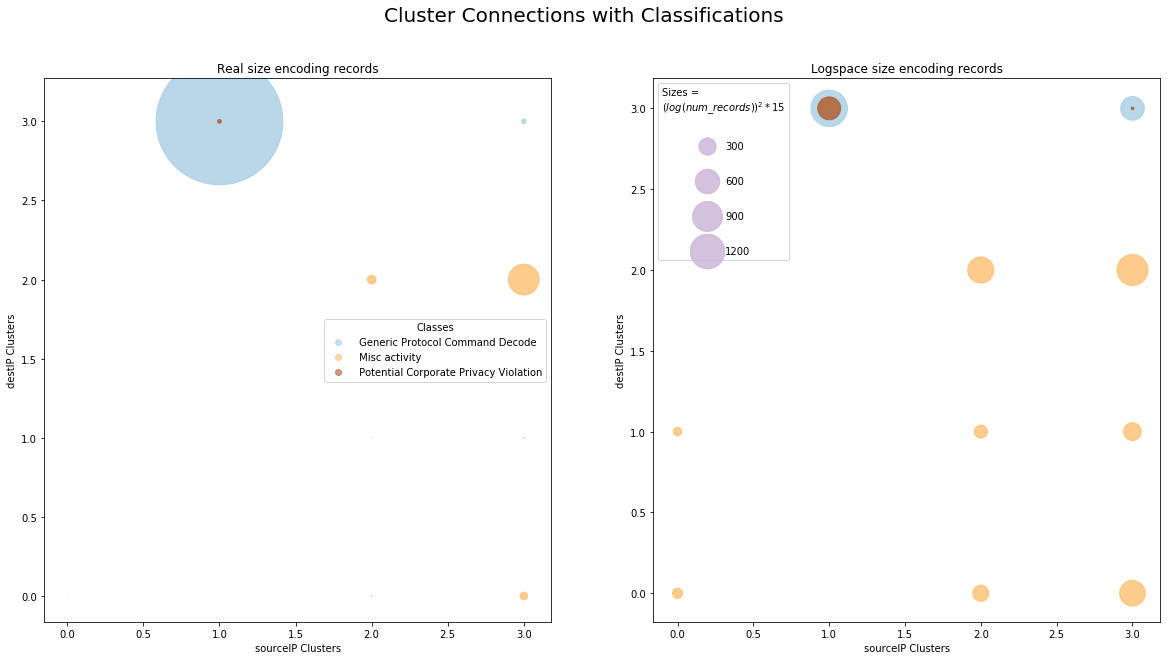
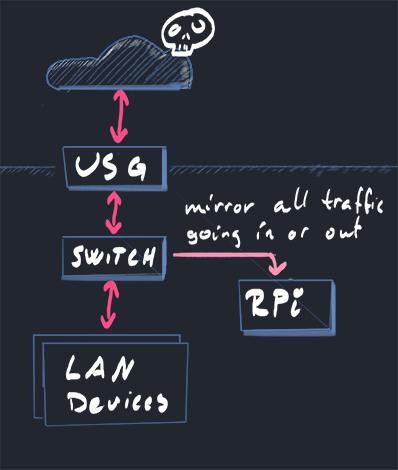
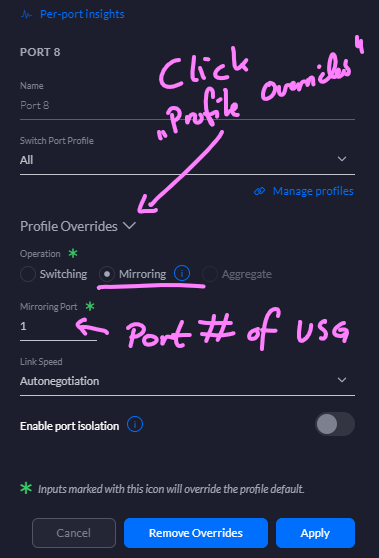
Secure network monitoring with elastic — Packetbeat + Suricata | by Carlos Cilleruelo | InfoSec Write-ups