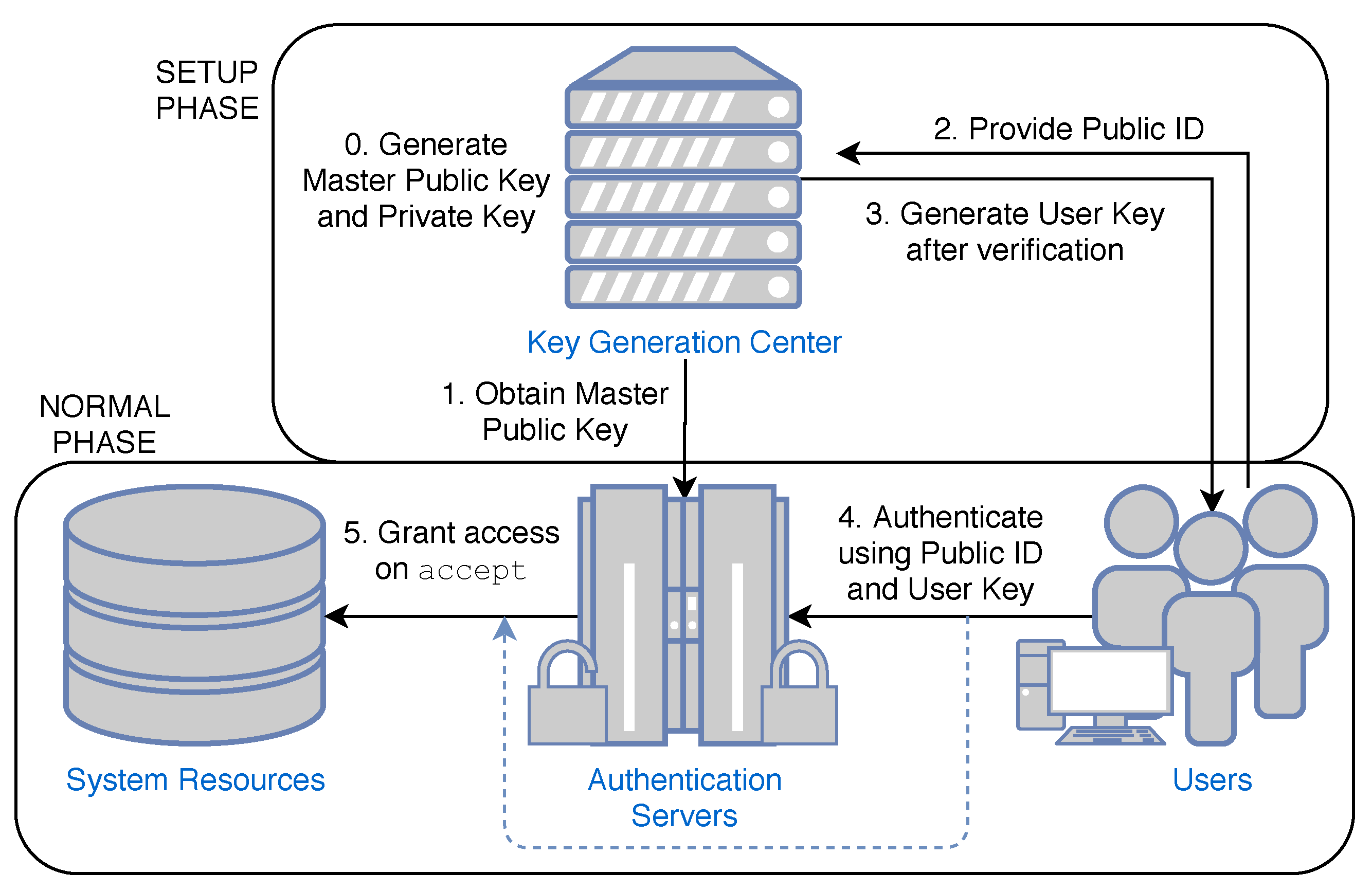
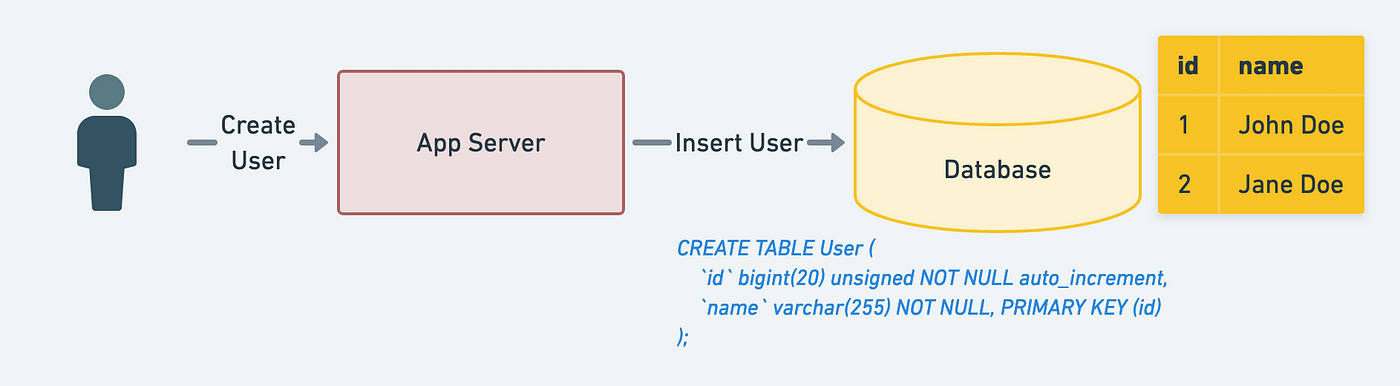
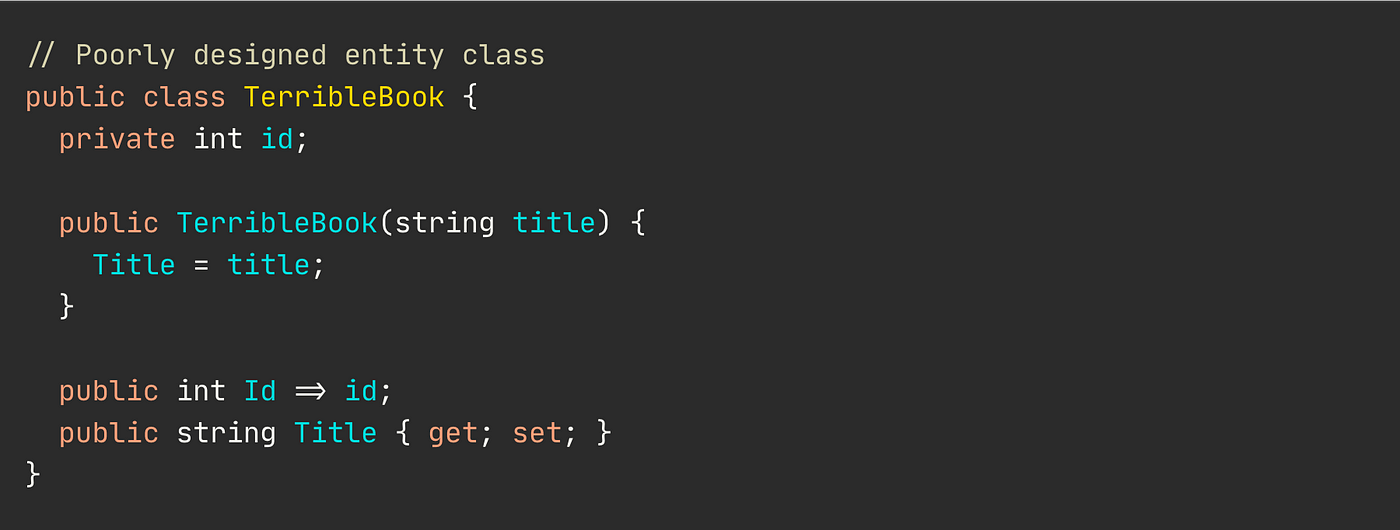
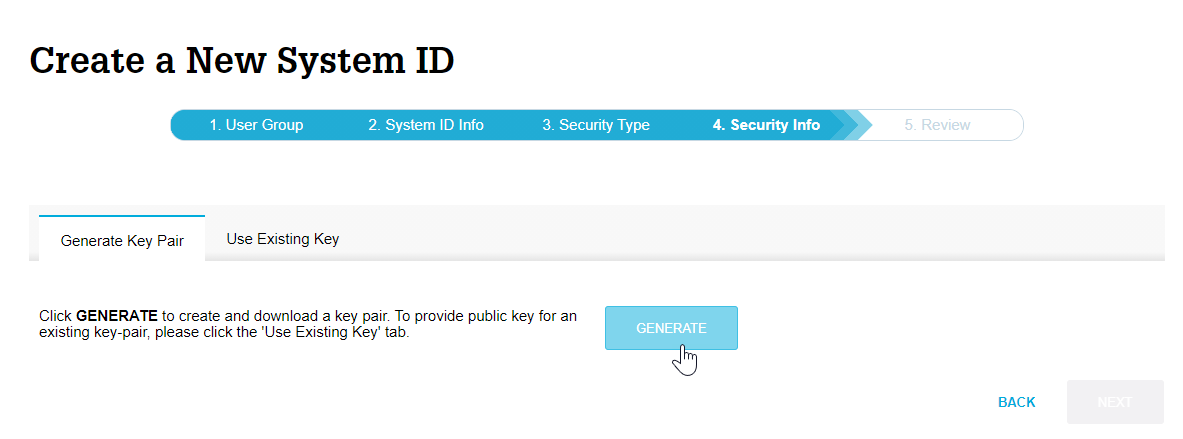
Trusted Generation of Public Keys — Based on Your Identity | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
![Free] CloudUrls An extension to generate URL from Cloudinary Public Id - Extensions - Niotron Community Free] CloudUrls An extension to generate URL from Cloudinary Public Id - Extensions - Niotron Community](https://community.niotron.com/uploads/default/original/2X/6/6002b52afc6ea65851270c3a6ddb50510de0a0b2.png)
Free] CloudUrls An extension to generate URL from Cloudinary Public Id - Extensions - Niotron Community
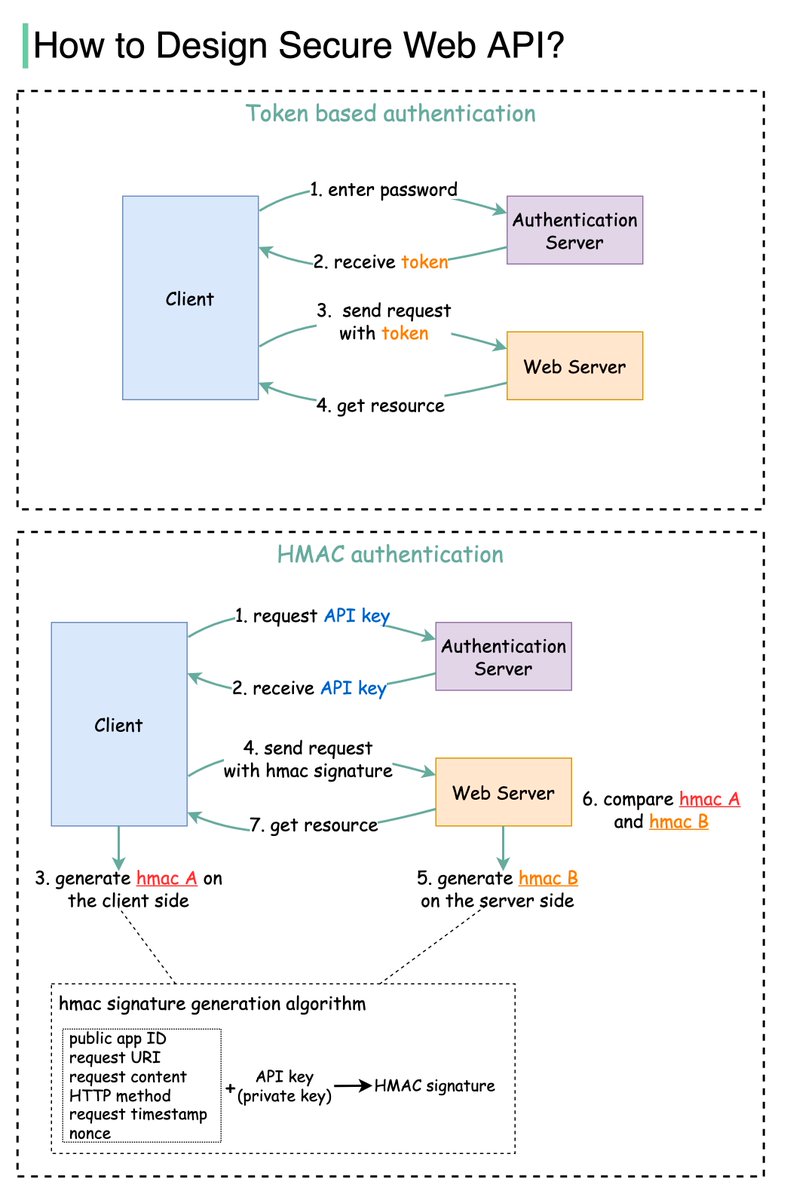
טוויטר \ Alex Xu בטוויטר: "2. HMAC (Hash-based Message Authentication Code) authentication The diagram below illustrates how they work. 𝐓𝐨𝐤𝐞𝐧 𝐛𝐚𝐬𝐞𝐝 Step 1 - the user enters their password into the client,