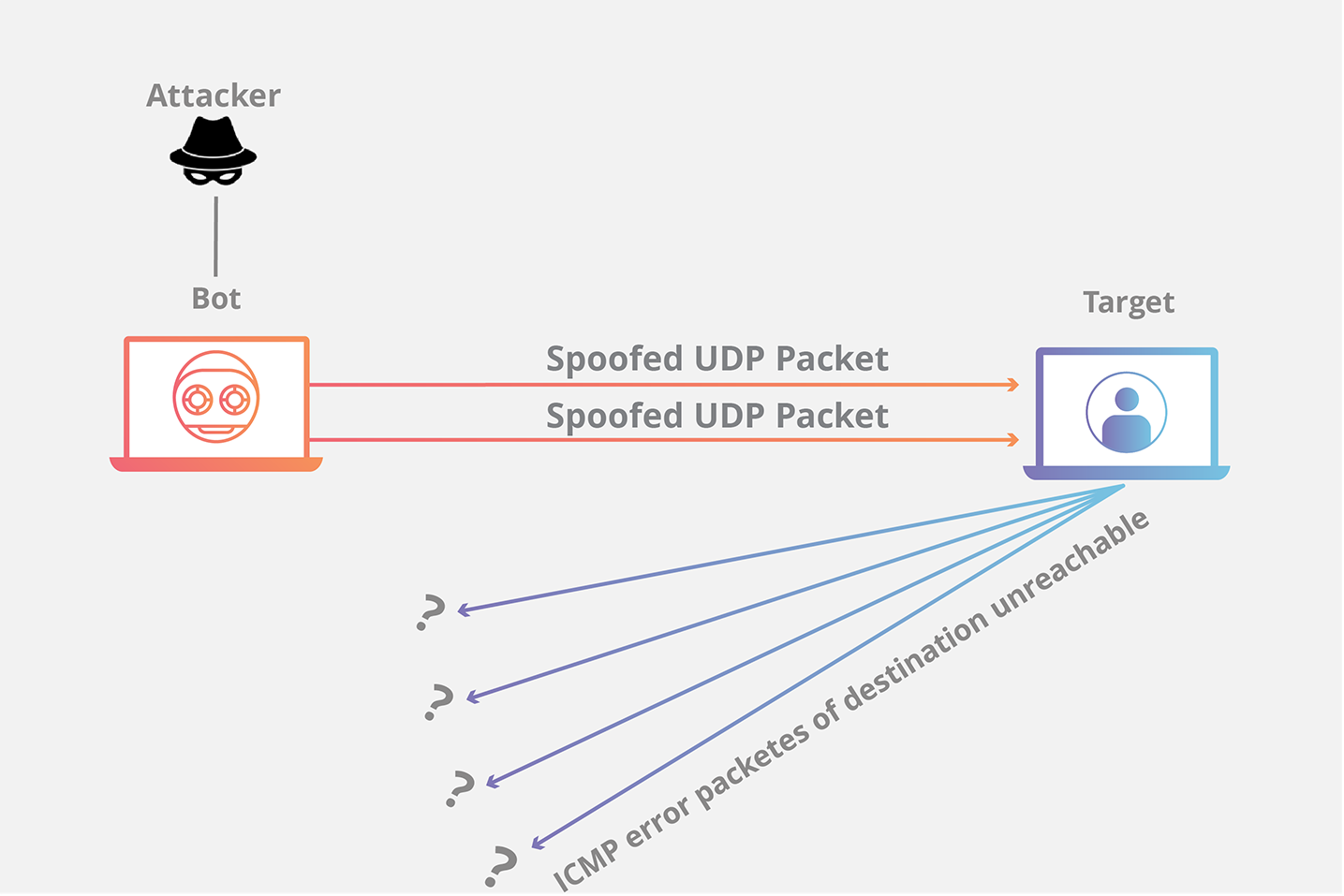
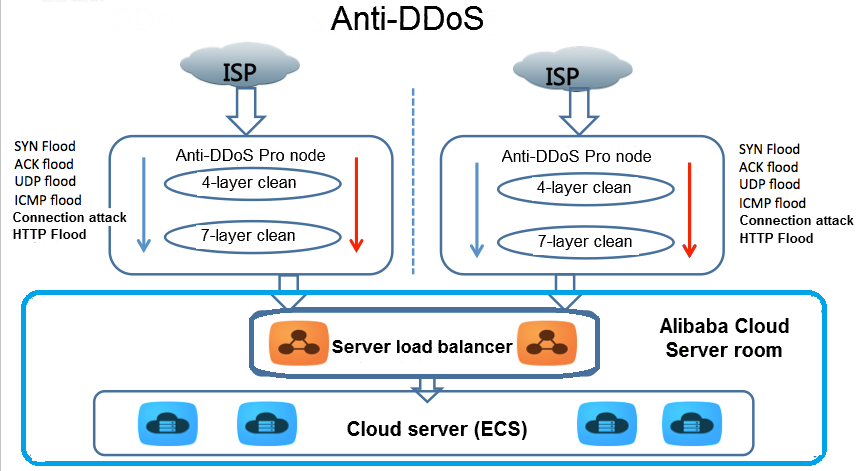
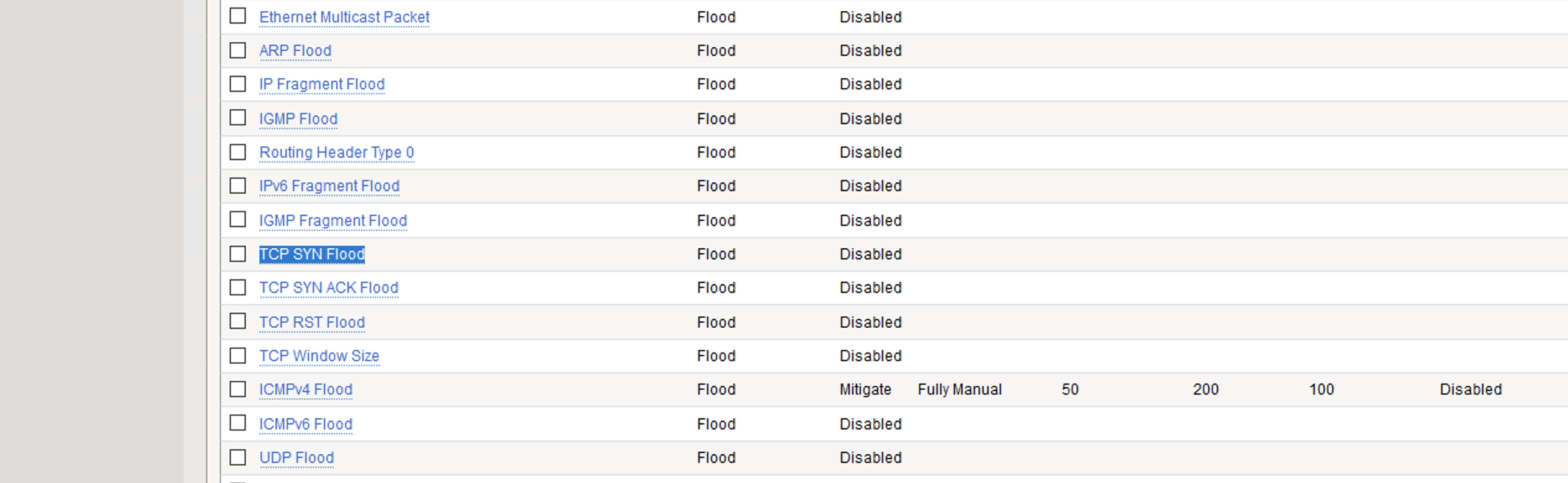
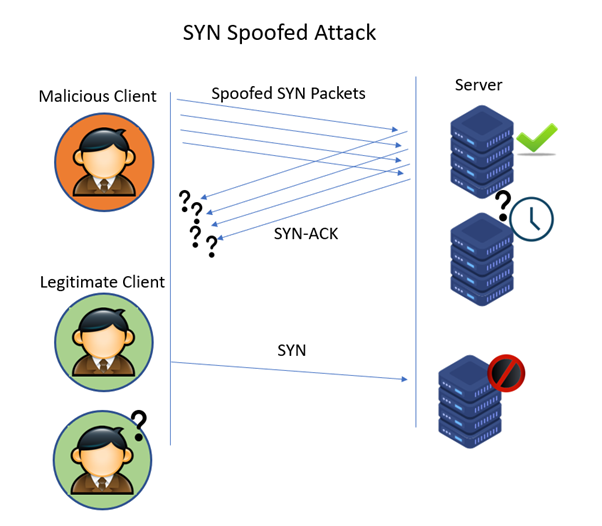
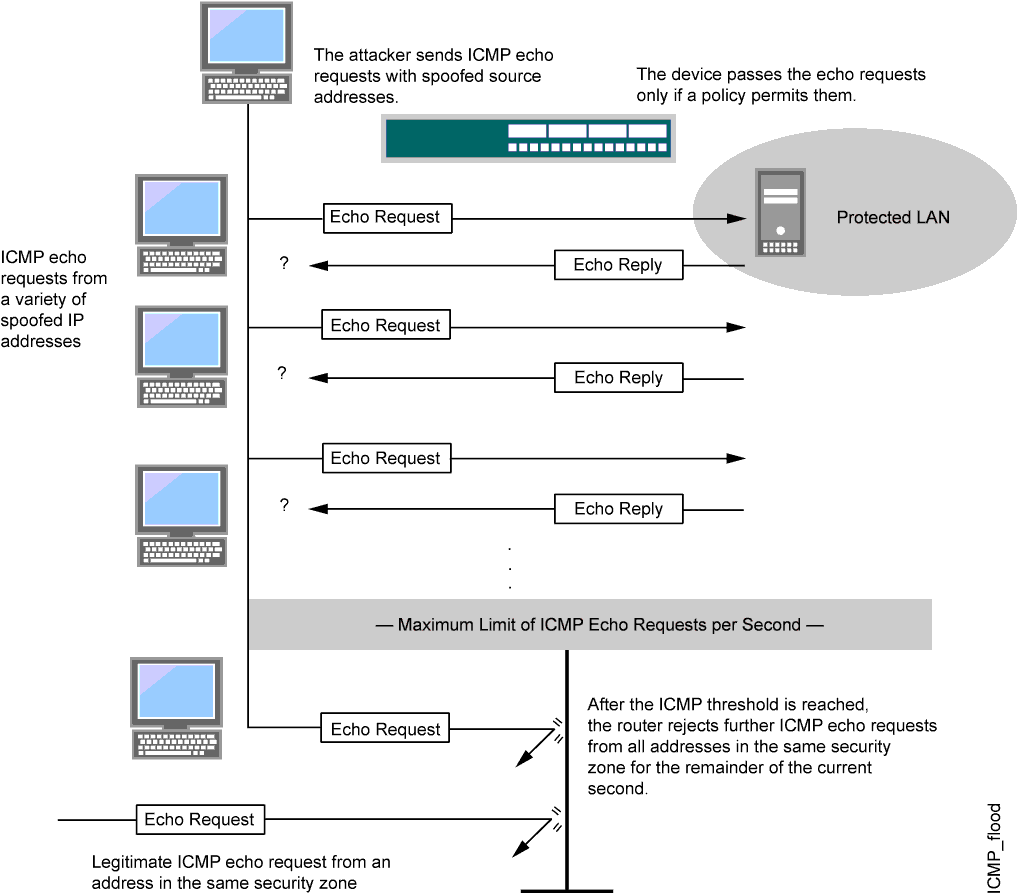
Detecting SYN flooding attacks based on traffic prediction - Wang - 2012 - Security and Communication Networks - Wiley Online Library
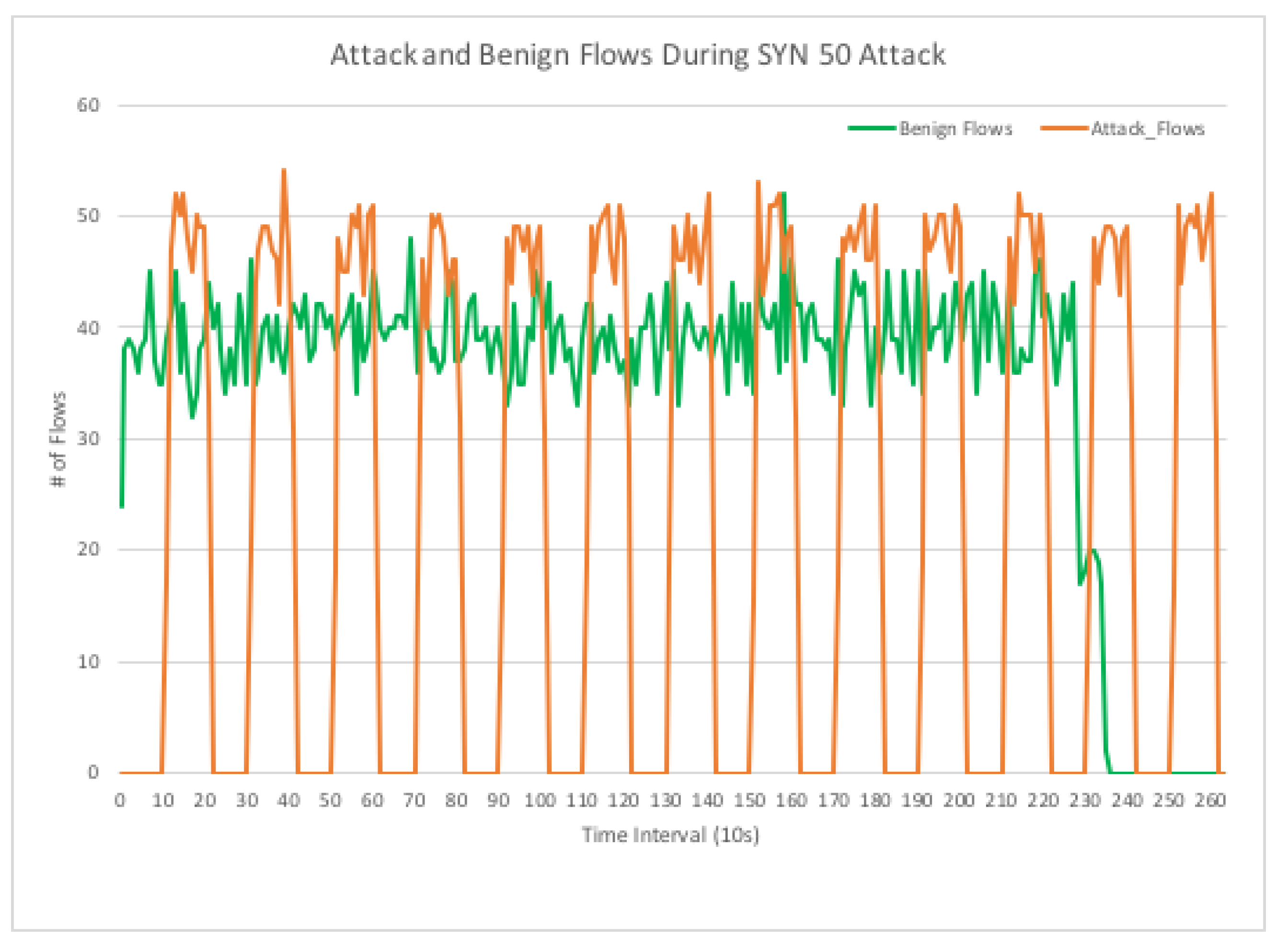
Electronics | Free Full-Text | On the Detection of Low-Rate Denial of Service Attacks at Transport and Application Layers | HTML

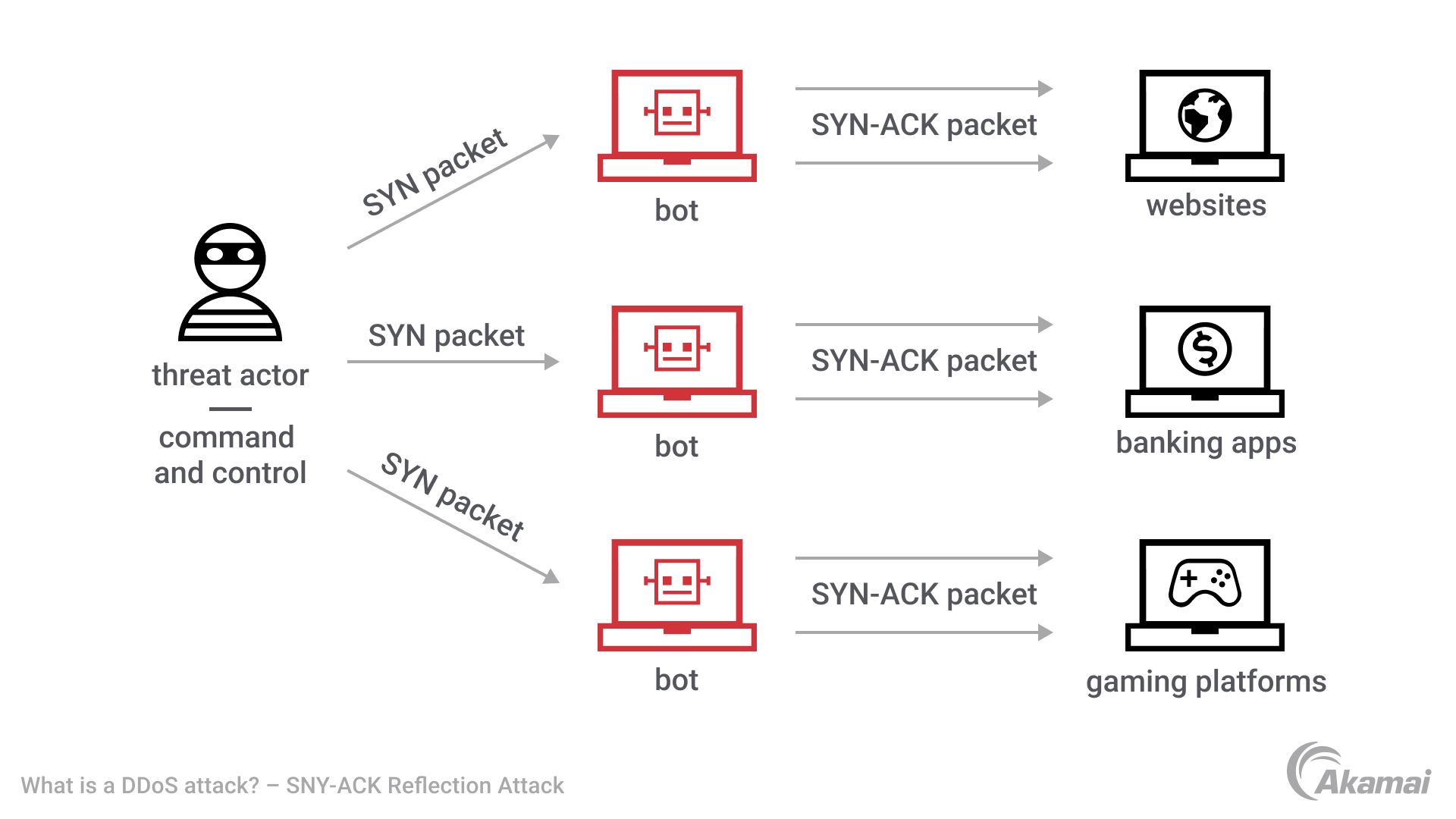
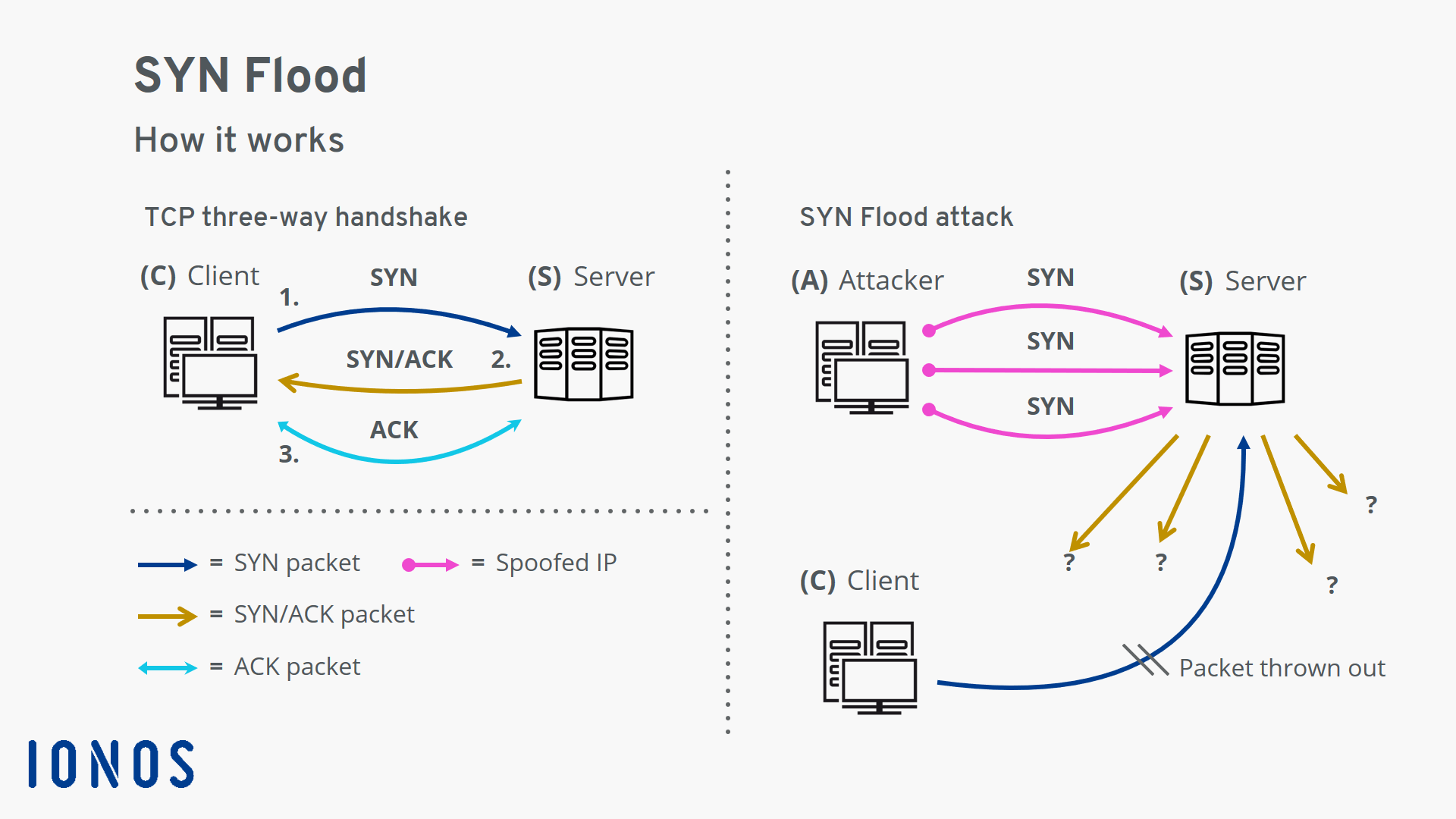
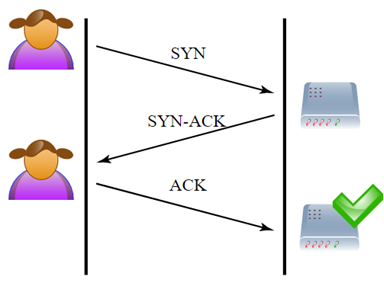
SYN flooding attack detection by TCP handshake anomalies - Bellaïche - 2012 - Security and Communication Networks - Wiley Online Library
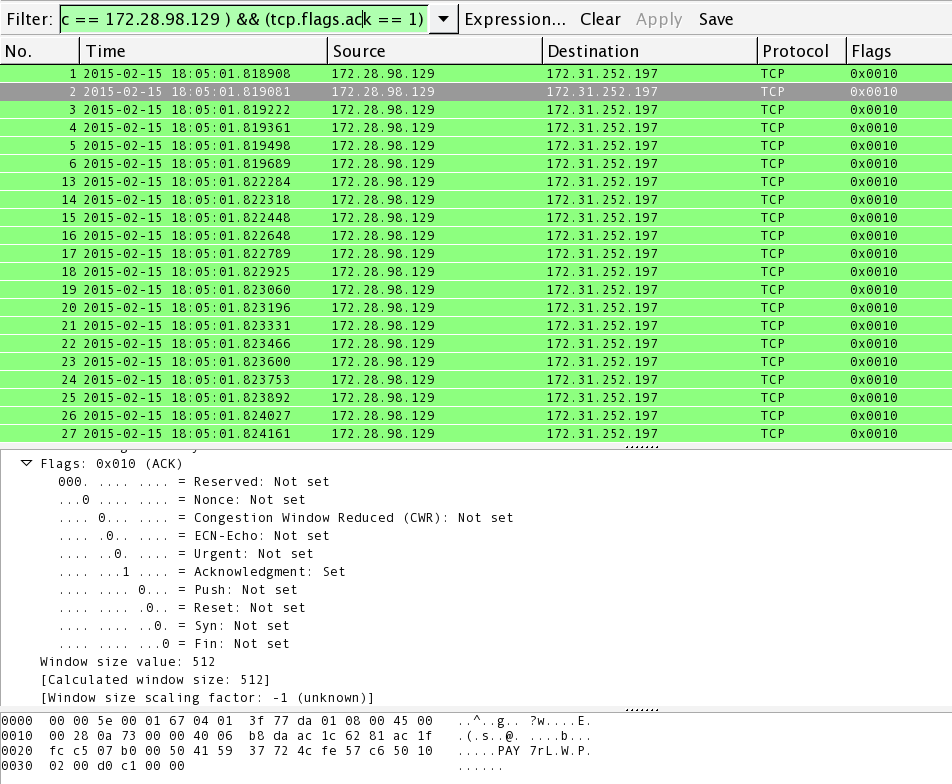
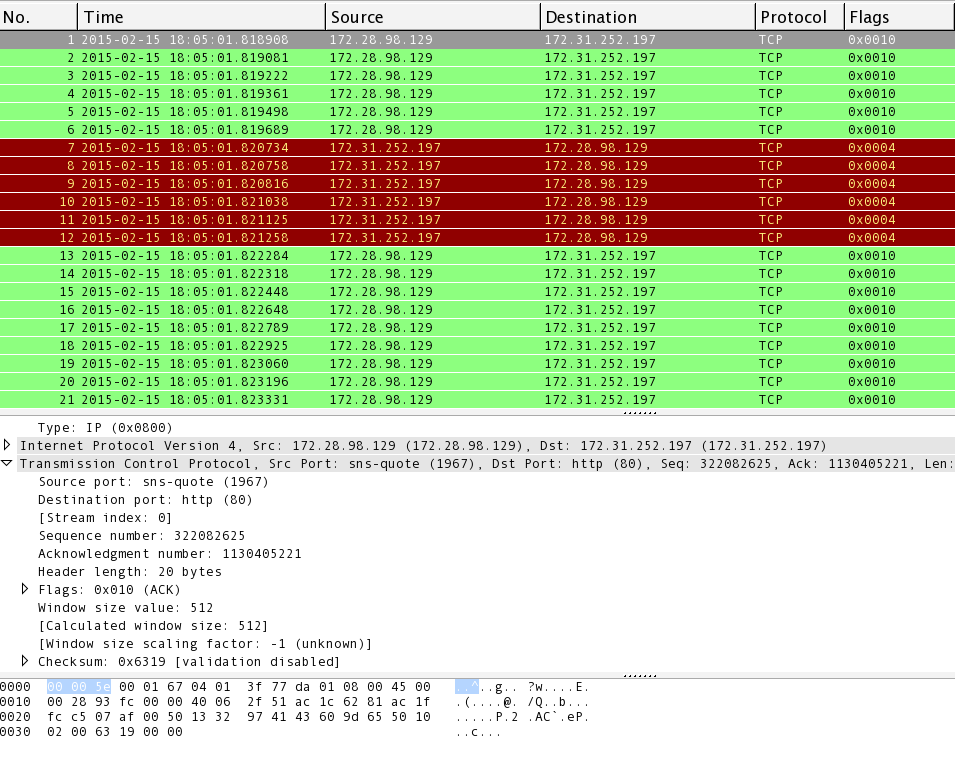
Denial of Service (DoS) attack identification and analyse using sniffing technique in the network environment
Denial of Service (DoS) attack identification and analyse using sniffing technique in the network environment