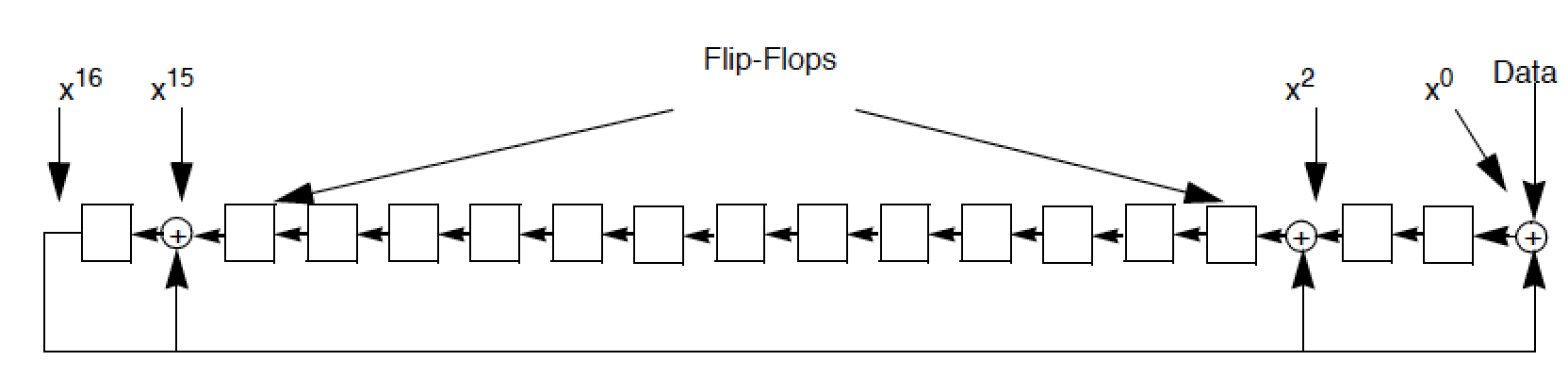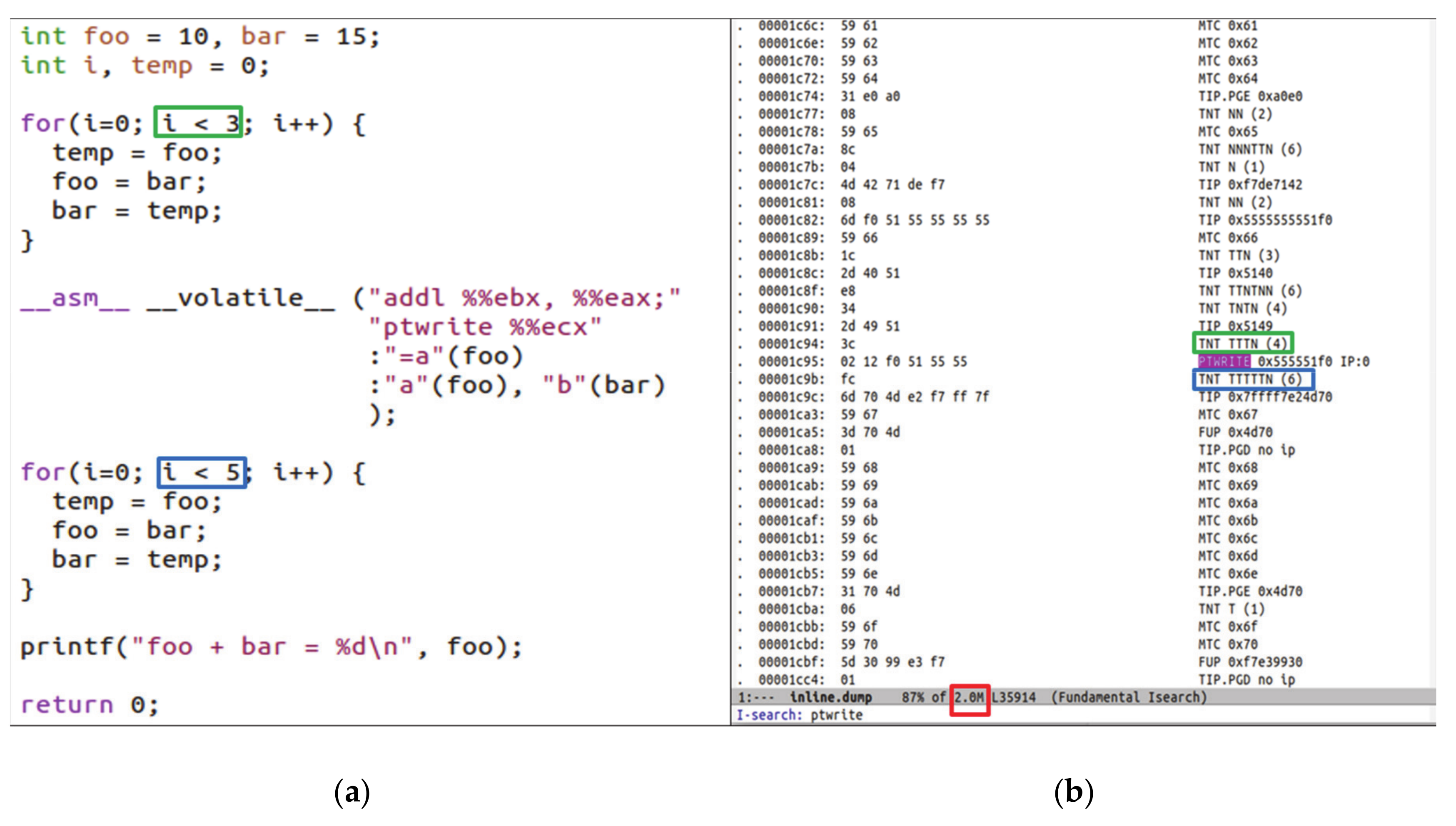
Electronics | Free Full-Text | Symmetric-Key Cryptographic Routine Detection in Anti-Reverse Engineered Binaries Using Hardware Tracing | HTML

Cryptography for Internet and Database Applications: Developing Secret and Public Key Techniques with Java | Semantic Scholar


![What Is AES Encryption? [The Definitive Q&A Guide] What Is AES Encryption? [The Definitive Q&A Guide]](https://www.trentonsystems.com/hs-fs/hubfs/2-1.png?width=1920&name=2-1.png)