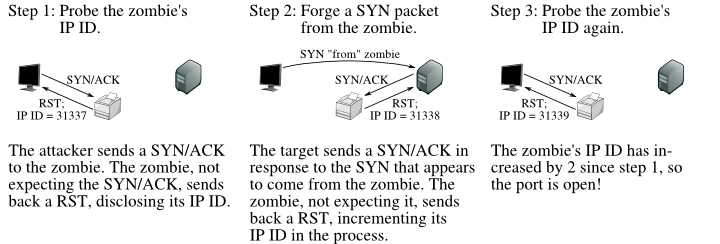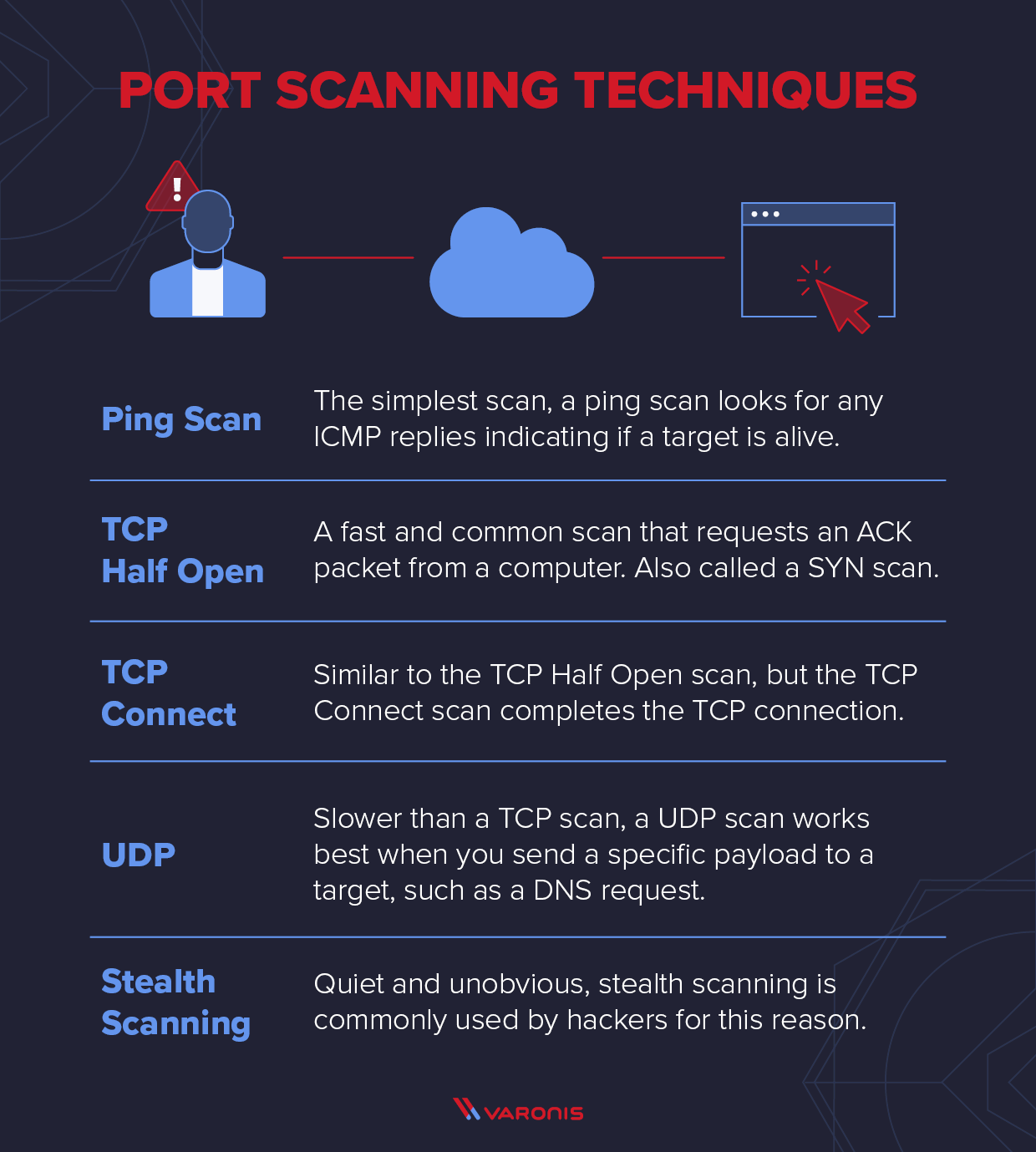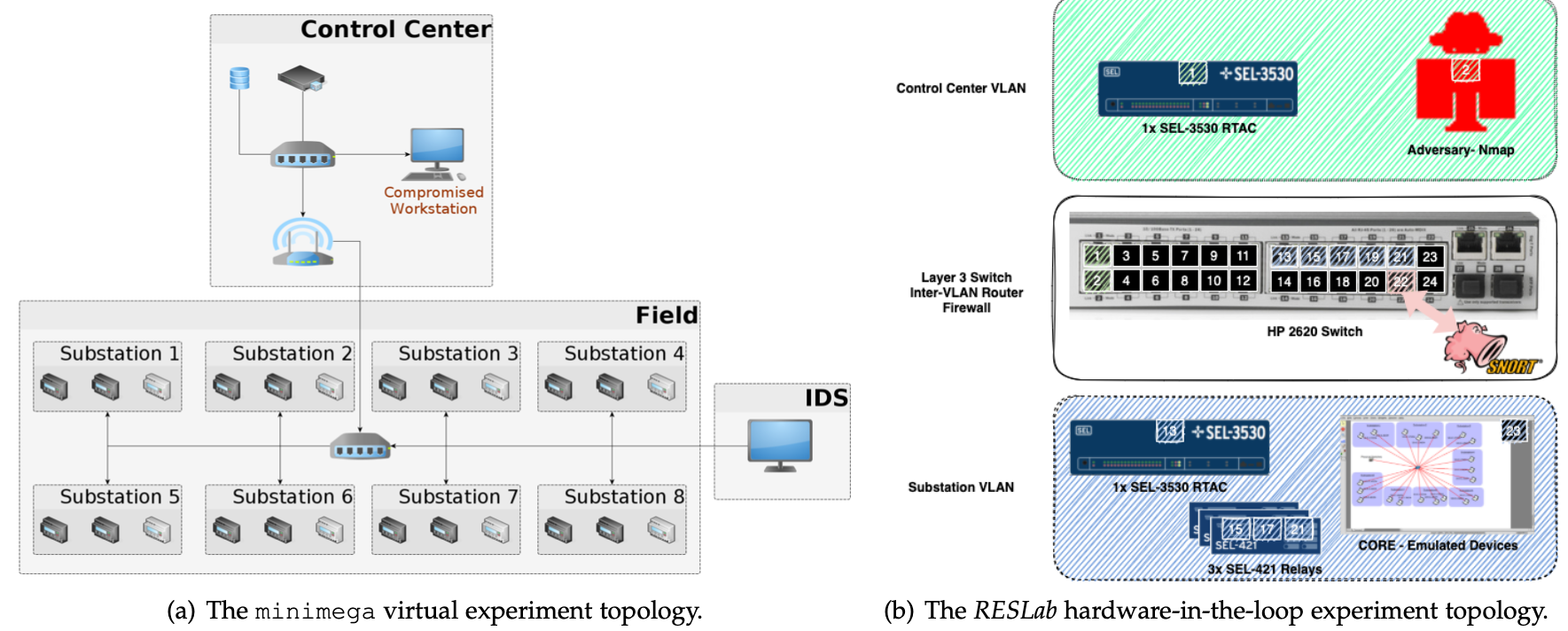
Dataset of Port Scanning Attacks on Emulation Testbed and Hardware-in-the-loop Testbed | IEEE DataPort
![PDF] Alternative Engine to Detect and Block Port Scan Attacks using Virtual Network Environments | Semantic Scholar PDF] Alternative Engine to Detect and Block Port Scan Attacks using Virtual Network Environments | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1b227ea0f684755183d7c36873c00a853f2e9f73/3-Figure1-1.png)
PDF] Alternative Engine to Detect and Block Port Scan Attacks using Virtual Network Environments | Semantic Scholar

Port scan attack successfully blocked through P4. Fig. 5: Scalability... | Download Scientific Diagram
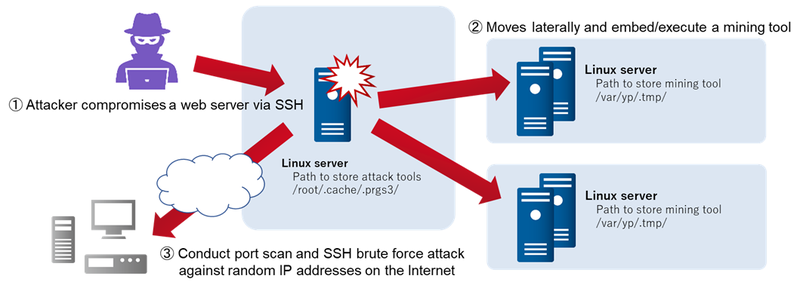
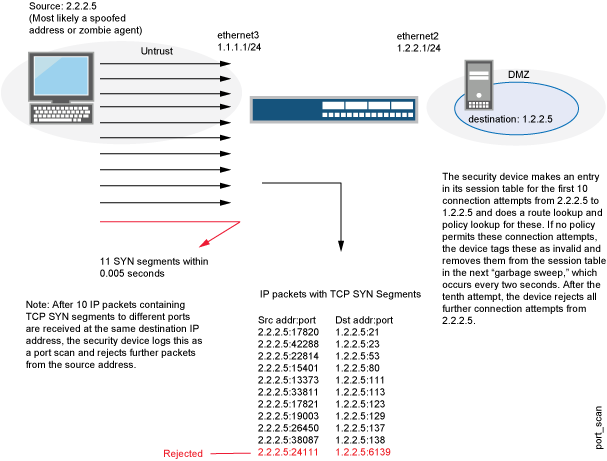
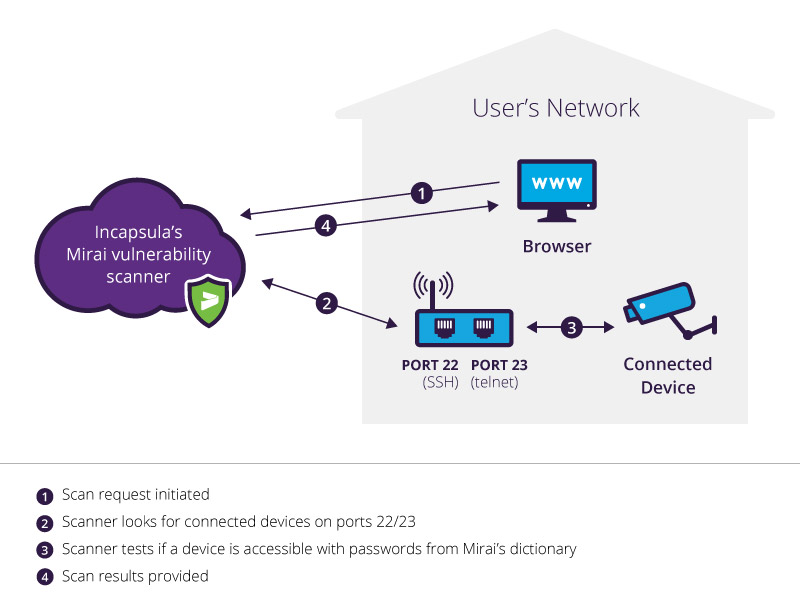




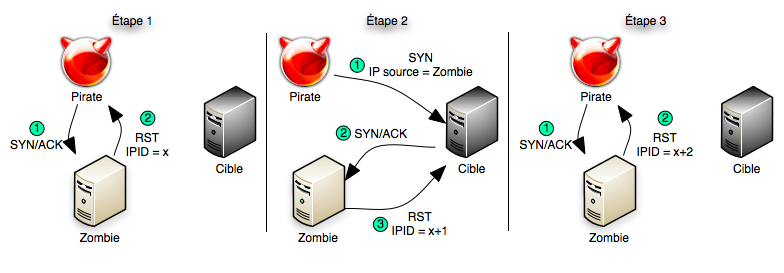


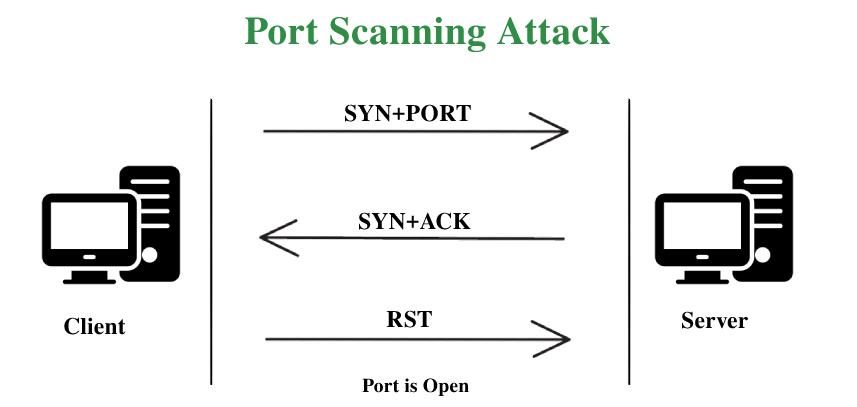
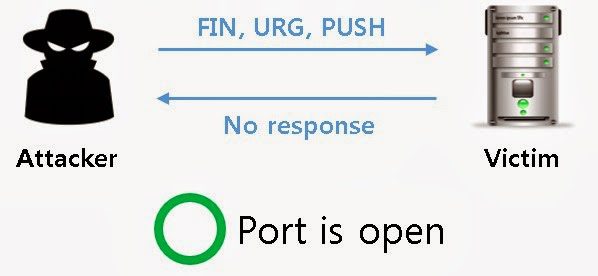
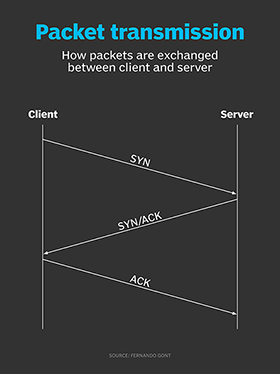
![KB2951] Resolve "Detected Port Scanning Attack" notifications (15.x – 16.x) KB2951] Resolve "Detected Port Scanning Attack" notifications (15.x – 16.x)](https://support.eset.com/storage/IMAGES/en/KB2951/KB2951Fig0-0a.png)